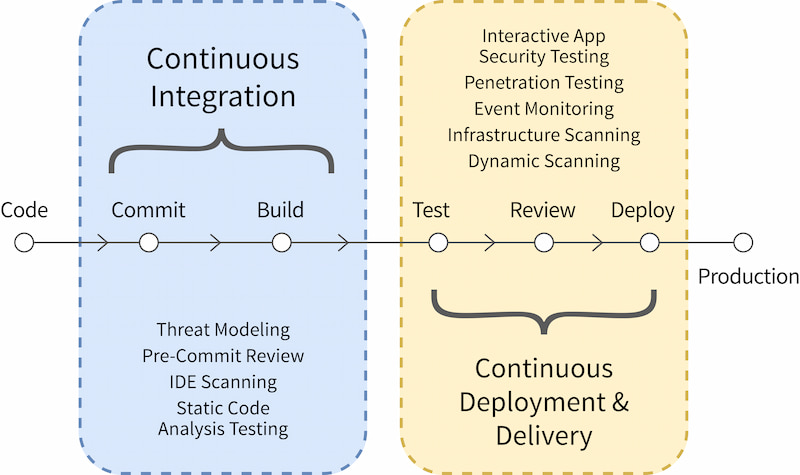
Securing continuous delivery pipelines requires a multi-faceted approach that involves alignment between different frameworks, technologies, and operational cultures. As a result, the security of a typical CD pipeline can be subdivided into a number of different aspects, including testing, IaC automation, runtime security, role-based access controls, threat modeling, source control, continuous monitoring, incident response plans, secure secrets, and vulnerability scanning.
Testing
Software security testing aims to identify threats and system weaknesses before they can be exploited in production. Used by QA teams and security experts alike, comprehensive testing helps to determine a system’s vulnerability score and provides guidance for hardening security measures.
Figure 2: Essentials of security within the CD pipeline
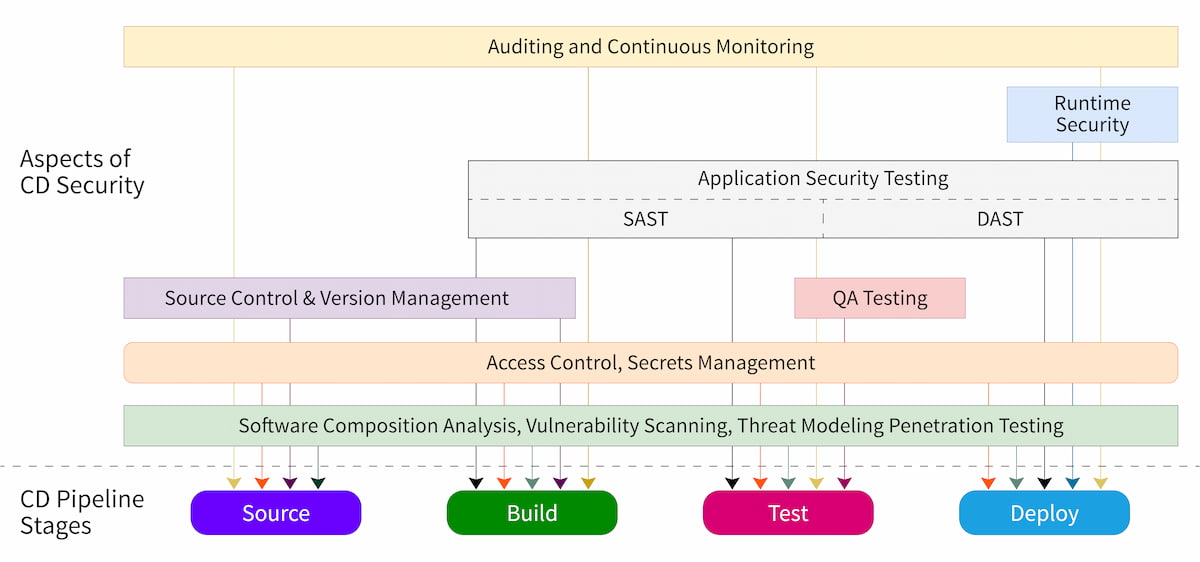
Security testing is often considered to be a broad term that includes a number of security mechanisms focused on different components of a workflow, including application security testing (AST), runtime application self-protection (RASP), software composition analysis (SCA), vulnerability scanning and penetration testing, and quality analysis (QA) testing.
Application Security Testing
Application security tools scan, analyze, and report the security posture of an application across different phases of the CI/CD pipeline. An AST mechanism is primarily categorized into the groups shown in the table below:
Table 1
Category |
Purpose |
Benefits |
Static application security testing (SAST) |
- Follows a white-box approach.
- Requires thorough understanding of underlying technology.
- Helps analyze the app for inherent security gaps within the source code, libraries, frameworks, and various software components used.
|
Identifies vulnerabilities such as:
- Code/command injection
- Directory indexing
- Insufficient transport layer protection
- Credential leakage
|
Dynamic application security testing (DAST) |
- Follows a black-box approach.
- Helps security teams write tests without learning the fundamentals of the app’s source code.
- Scans exposed external interfaces of an app to uncover runtime vulnerabilities.
|
Identifies vulnerabilities such as:
- App misconfiguration
- Improper input handling
- HTTP request smuggling
- Content spoofing
- Cross-site scripting
|
Interactive application security testing (IAST) |
- Combines SAST and DAST to widen the range of effectiveness.
- Although purpose-built to run and scan apps during runtime, IAST also compiles source code similar to SAST tools.
|
Remediates CD security flaws much quicker by identifying root cause of runtime issues and pinpointing specific code segments causing an error. |
Runtime Application Self-Protection
RASP is an advanced technology that has evolved over time to respond to security vulnerabilities and attacks in real time. The tool runs on an application server to help obtain collective visibility of the application's source code and underlying runtime components. RASP protection tools are primarily used to detect active threats while sniffing out and isolating malicious actors. While RASP can be customized differently for prevention tactics, the most common approaches are to either issue an alert, terminate the session, or both.
Software Composition Analysis
SCA automates the identification of open-source software vulnerabilities used within the application stack. A typical software composition analysis involves scanning the container images, manifest files, source code, and binary files to come up with a Software Bill of Materials (SBOM), which is compared against a database of known vulnerabilities for security posture evaluation. SCA tools also enable security teams to evaluate the code quality, license limitations, and compliance of open-source software used within an existing workflow.
Vulnerability Scanning and Penetration Testing
Vulnerability scanning and penetration testing are active threat identification processes that involve inspecting the application from an attacker’s point of view. Though the processes are mostly used as two separate approaches, they can also be used as concurrent steps to identify application flaws.
As the first step, vulnerability scanning helps proactively identify weaknesses within the enterprise network. Once these vulnerabilities are identified, security professionals perform penetration tests to see how the attacker can exploit them to orchestrate attacks. Beyond identifying system weaknesses, threat hunting functionalities also help determine the effectiveness of security controls in place and flag enhancement opportunities.
Quality Analysis Testing
QA testing is the process of evaluating whether the software performs to customer expectations and the required standards of the user experience. Beyond testing the functional and technical performance of software, QA tests assess the product’s usability, compatibility, and known vulnerabilities.
IaC Automation
Infrastructure as Code (IaC) enables the provisioning and management of infrastructure resources across multiple deployment environments using declarative text files. Developers can leverage dedicated CD and DevOps processes for security testing, version control, application updates, and security fixes. With automated IaC tools, organizations can proactively enhance the security posture of an application’s infrastructure while fostering collaboration between security, development, and operation teams.
Runtime Security
Runtime security encompasses various activities focused on identifying and remediating security flaws of a production environment. Securing a runtime primarily involves analyzing the application’s source code and server activity — as well as monitoring network activity — for any defects and potential threats.
On account of its multiple underlying components and sub-processes, securing a runtime often involves leveraging various tools and a collection of security controls, including:
- Runtime application self-protection (RASP)
- Web application firewall (WAF)
- Log analysis
- Vulnerability scanning
- Container security
Role-Based Access Control
Role-based access control (RBAC) is one of the most widely adopted mechanisms for governing permissions and actions of a CD pipeline at the component/sub-workflow level. The mechanism forms the foundation of CD security by relating data privacy, confidentiality, compliance, and access to specified resources and processes.
RBAC helps developers implement resource access as a function of the firm’s organizational structure, helping to group users efficiently based on seniority or functions performed. To achieve this, RBAC systems implement an innate separation of duties, breaking down sensitive functionalities into smaller units, thereby reducing the attack surface in the event of an account breach.
Threat Modeling
Threat modeling involves an elaborate analysis of how a system operates while examining the combination of user behavior with data flows across network components. Ethical hackers and security researchers commonly use threat modeling to identify potential security gaps and attack mechanisms of a tech stack to help mitigate known and unknown vulnerabilities. Though the process involves integrating security checks throughout the development lifecycle to identify and remediate security issues, the approach is considered one of the most critical security practices during the initial phases of system design.
Source Control
Version/source control management (SCM) enables cross-functional teams to collaborate liberally without the apprehension of unwanted changes and updates. Leveraging a centralized branch as a single source of truth for all interlinked systems of the workflow, SCM tools retain committed changes in an organized and well-structured format. SCM tools also maintain comprehensive version history that allows CD security teams to roll back or undo erroneous updates.
Continuous Monitoring
Continuous monitoring is one of the core processes that automates the identification of security flaws and compliance errors throughout the software development lifecycle. The mechanism essentially blends observability into the continuous change processes that characterize a typical CD pipeline. Continuous monitoring covers multiple facets, including:
- Comparison of deployments over time
- Daily trend analysis
- Vulnerability scanning, reporting, and remediation
- Security incident alerting
- Retrospective analysis of security incidents
Besides helping to identify error sources and security vulnerabilities, continuous monitoring also aids enterprises in measuring the user experience and KPIs. Adoption of such monitoring tools allows QA teams to receive prompt feedback on how a recent security update affects users, subsequently helping to refine the security strategy.
Incident Response Plans
An incident response plan allows organizations to maintain clarity and an escalation matrix during a security crisis. The plan outlines the systematic handling of security attacks to ensure such incidents cause minimal impact to the organization’s assets, financials, and reputation. Diligently designed incident response plans help CD security teams protect crucial data, maintain trust, and safeguard the firm’s revenue while resolving a security crisis.
Secure Secrets
Secrets such as user credentials, configuration files, API keys, tokens, and other sensitive information exist throughout the lifecycle of a CD pipeline. These secrets are considered one of the primary sources of data leakage and hence, should be consistently hidden, protected, and governed.
While seamless delivery of code through different phases of the SDLC is crucial, it is equally important to maintain robust security of secrets across all stages of the workflow. The adoption of secret management systems that streamline the storage and management of access management components is often considered a key factor that prevents unauthorized access of system resources without impacting delivery. Some of these solutions also offer encryption, key management, and identity management services, further simplifying the secure access to organizational data and resources.
Open Source Vulnerability Scanning
Organizations that rely on third-party-developed open-source software often tend to overlook certain features and vulnerabilities of their source code. On account of the open source nature of such software, hackers typically possess detailed intricacies of the code along with the list of known vulnerabilities. Unsurprisingly, mitigating attacks in such workflows requires focused vulnerability scans of open-source components to identify weaknesses before they are exploited.
Vulnerabilities in open-source software commonly arise due to a number of factors, including:
- Inexperienced developers and maintainers of the open-source code
- Lack of coding best practices
- Outdated/unpatched code



{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}
{{ parent.urlSource.name }}