Information Security: AI Security Within the IoT Industry
This article immerses the reader into the AI Security in the IoT industry, providing more understanding of the different kinds of “securities” that underlie the topic.
Join the DZone community and get the full member experience.
Join For FreeAs the digital age progresses, we find ourselves amidst numerous ways of transmitting and storing information. From the smart devices that indwell our homes to the advanced artificial intelligence systems powering industries, the intertwining of technology with our daily lives has never been so intricate. Yet, with this profound integration comes a tough reality: the more channels and repositories for information we create, the larger the expanse for potential threats. These threats not only increase in number but also the magnitude of their impact. It is more evident when it comes to AI security within the IoT industry. While introducing its revolutionary potential, IoT also presents novel security challenges that demand our highest attention.
This article aims to immerse the reader into the world of AI Security in the IoT industry, exploring the vulnerabilities, the potential threats, and the strategies for ensuring a safer digital future, as well as providing the reader with more understanding of the different kinds of “securities” that underlie the topic.
IT Security, Information Security, and Cybersecurity: Understanding the Distinctions
Nowadays, terms like IT Security, Information Security, and Cybersecurity are often thrown around interchangeably. This inevitably leads to widespread confusion about their meanings, even among professionals in the tech industry. As we go deeper into the realms of IoT and AI security, it's vital to differentiate between these terms. It might be perplexing for the first time, but we will try to unfold this multilayer system step by step with some illustrations.
Let’s first look at the diagram.
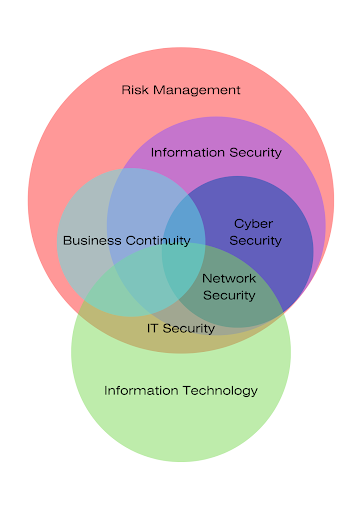
Dealing with security is what we call risk management. Risk management can lie beyond any of the IT-related issues, but at some point in the modern world, inevitably, it intersects with Information Technology. This intersection comprises IT Security, Information Security, and Cyber Security. Let us examine each of them closer.
IT Security focuses specifically on the protection of digital data and the systems that handle it. It emphasizes the safeguarding of computer systems from theft, damage, or unauthorized access. This might involve measures to protect against malware, phishing, and more.
If you look at the types of IT Security, you might see some new aspects. It includes Network Security, Internet Security, Endpoint Security, Cloud Security, and Application Security.
Information Security, at its core, is about protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction. The primary goal of InfoSec is to maintain the confidentiality, integrity, and availability of data. Types of Information Security encompasses Application Security, Cloud Security, Infrastructure Security, Incident Response, Cryptography, Disaster Recovery, and Vulnerability Management.
Cybersecurity, in turn, is included in InfoSec and comprises its main part. Cybersecurity specifically deals with protecting systems, networks, and data from cyber threats. Nevertheless, Cybersecurity is included in InfoSec and has a partial overlap with IT Security. Cybersecurity strategies might involve firewalls, intrusion detection systems, encryption protocols, and others. If you want to know more about the types of Cybersecurity, it encircles Network Security, Cloud Security, Endpoint Security, Application Security, and IoT Security.
Within the framework of Cybersecurity, an IoT breach refers to a cyber assault that focuses on an Internet of Things (IoT) device or system. Once compromised, the cybercriminal can take over the device, extract information, or incorporate it into a collection of compromised devices, forming a botnet to initiate DoS or DDoS attacks.
The frequent appearance of such malicious IoT botnet activities is highlighted in the recent findings by the Nokia Threat Intelligence Lab, which shows a great wave since 2022. The insights from Kevin McNamee, the founder of the Lab, suggest that a significant portion, approximately 60%, of the observed malware activity in networks can be attributed to IoT botnets.
In the interview dedicated to the increase of the mobile botnet in the 5G era, Kevin McNamee discusses how 5G networks offer enhanced security compared to previous generations, especially within the mobile core. With the advent of the mobile era, which is the current state of affairs, distinct from the previous PC era, the number of active mobile users significantly escalated. With the rise of mobile and IoT devices, 5G's increased bandwidth has expanded the potential attack surface, especially with the growth of IoT devices. An innovative 5G feature, "network slicing," allows for specialized security measures designed for different applications.
However, to say attacks on the IoT sphere keep pace with its development would be an understatement. With the advancement of the powers of AI, attackers can invade one’s personal life through the gadgets used daily and utilize them for the purposes they pursue.
In the American series 'Next,' the vulnerabilities within the IoV (Internet of Vehicles) sector are brought to the forefront. Here, after noticing a series of sophisticated, non-human cyber-attacks, computer scientist Richard Weiss grows increasingly paranoid about using electronics and starts to avoid them altogether. Despite his precautions, he's targeted in a vehicular attack initiated by artificial intelligence. The attack led to a near-fatal accident, with the only evidence of the cyber threat being a snapshot of code he saved before his computer was wiped clean. Such narratives shed light on the potential hazards posed when vehicles become more interconnected and reliant on technology, opening avenues for malicious AI-driven attacks.
Another illustration can be found in the more practicable scenario. Smart home devices, as reported by Verdict, are increasingly under scrutiny for their potential cybersecurity vulnerabilities. The article points out the fact many devices lack the infrastructure for security, such as a traditional operating system, and often come with hardcoded passwords, making them prone to breaches. Another concerning element is that one compromised device can serve as a gateway to others on the same network. Consequently, even a single weak link in a smart home ecosystem, whether it's a doorbell, camera, or even a fish tank, can jeopardize the entire network's security.
Furthermore, IIoT, or Industrial IoT, involves the integration of digital technologies into an industrial setting. At its core lies the Industrial Control Systems (ICS), which are specialized cyber devices regulating critical infrastructures, from transportation and energy to water systems. Given their role in vital infrastructures, any breach can have catastrophic consequences, as documented in various threat assessments and incidents.
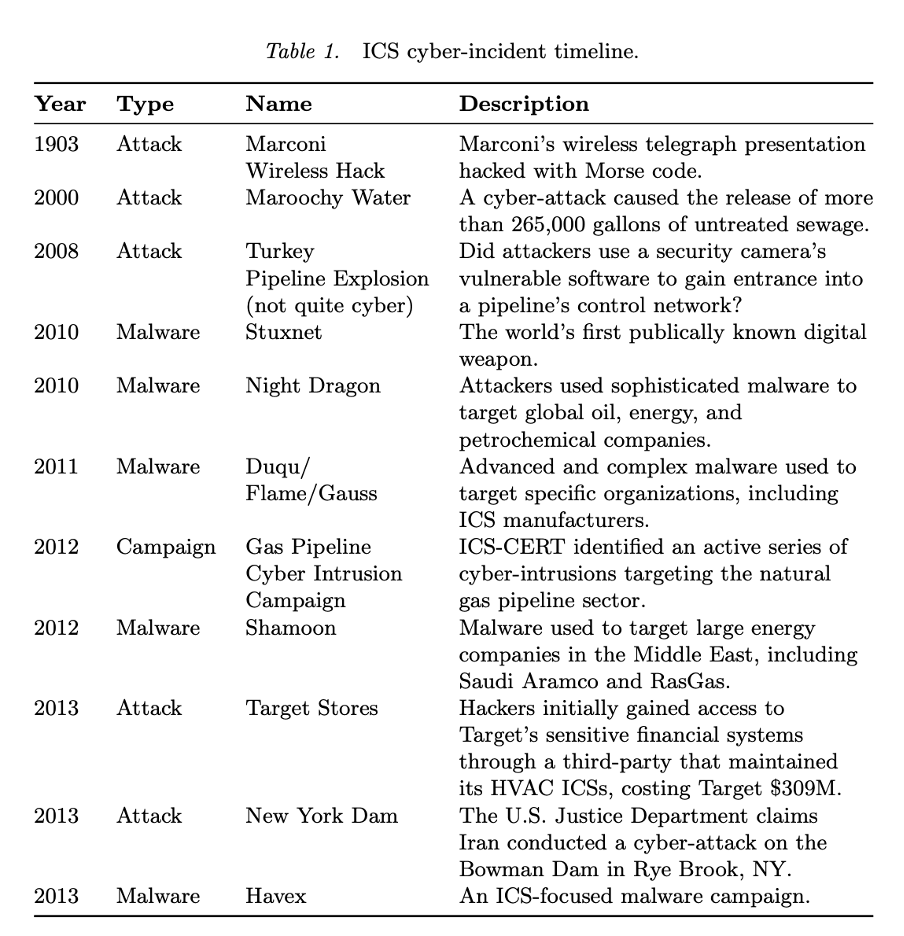
The 2012 ICS-CERT discovery of cyber-intrusions targeting the natural gas pipeline sector, mentioned in the History of Industrial Control System Cyber Incidents article (Hemsley, Kevin E., and E. Fisher, Dr. Ronald, 2018), depicts the potential devastation, with threats capable of destroying entire cities. In the same vein, the article provides a range of various attacks on such large and crucial industries as oil, petrochemical, and energy manufacturers.
The table drawn from the studies above below presents information from various sources, including cybersecurity firms, independent security experts, and news outlets. The compilation highlights major cyber threats, events, and campaigns impacting ICS devices and essential infrastructure (although the number of incidents is not limited to these instances). In certain instances, ICS devices were the direct targets; in others, they were either indirectly targeted or affected. As evident from the chart, cyber attacks present themselves in different forms and have various consequences. But it is crucial to remember the potential of AI attacks is immense. AI-driven attacks, say, on the nuclear energy industry could have consequences so catastrophic it could obliterate an entire country.
What Is AI Security and Its Role in IoT Safeguarding?
AI Security refers to the set of practices, strategies, and measures implemented to safeguard artificial intelligence systems, machine learning models, and related technologies from potential threats, vulnerabilities, and malicious activities. It encompasses a range of protective measures to ensure the integrity, confidentiality, availability, and ethical use of AI systems throughout their lifecycle. Types of AI Security include:
Data Security ensures the confidentiality, integrity, and availability of the data used by AI systems and encompasses encryption, access controls, secure data storage, and data anonymization to prevent unauthorized access or data leakage.
Privacy Preservation, as an integral part of AI Security, can be categorized into two domains. Differential Privacy encompasses methods that introduce managed disturbances into data to safeguard individual privacy without compromising the general usefulness of the data. In contrast, Federated Learning allows for spreading the training procedure over various devices to prevent the disclosure of raw data.
Information Security has several types as well. AI is related to all of them. For instance, AI systems can also be targets for malware and intrusion attempts. Implementing intrusion detection systems and real-time monitoring helps identify and mitigate such threats, that is, Vulnerability Management.
It is worth noting that security measures need to be continually monitored and adapted as new threats emerge and AI systems evolve. Threat Intelligence, which grants staying informed about evolving threats and vulnerabilities, and Patch Management, implying regularly applying updates and patches to fix vulnerabilities, pinnacle the list of necessary methods of protection.
Besides those above, there is a need for Incident Response and Recovery. Security Incident Response includes protocols for addressing security breaches or attacks. Disaster Recovery, as an aftermath measure, helps plan to restore normal operations after an incident.
Explainability and Transparency, as another level of AI Security, ensures that AI models are explainable and transparent. It is crucial for identifying vulnerabilities and understanding how decisions are made. Transparent models are easier to audit and debug.
Human-AI Interaction Security assures that the interactions between humans and AI systems are secure. This includes protecting user data, preventing impersonation attacks, and ensuring that AI-generated outputs are not exploited for malicious purposes.
Model Security, in turn, focuses on protecting the AI models themselves from attacks such as adversarial attacks, model inversion attacks, and poisoning attacks, such as:
- Adversarial Perturbations: Malicious inputs crafted to deceive AI models into making incorrect predictions.
- Transfer Attacks: Adversarial attacks that work across different AI models.
- White-Box and Black-Box Attacks, which depend on the attacker's knowledge of the target model's architecture.
Bias and Fairness Security in AI involves techniques to detect and diminish biases in data and models while ensuring predictions are equitable. This level encircles Bias Mitigation — techniques to identify and reduce biases in training data, and Fairness-aware Learning, created to design models that make fair predictions across different demographic groups.
Lifecycle Security encapsulates measures that should be implemented throughout the entire lifecycle of an AI system, from design and development to deployment and retirement. This includes secure coding practices, regular updates, and proper disposal of systems.
Regulatory Compliance establishes that AI systems must comply with relevant regulations, such as data protection laws (e.g., GDPR), industry-specific regulations, and ethical guidelines. This brings us to examining AI Ethics Security, which ensures AI systems are developed and deployed ethically due to Ethical Use Policies.
Finally, Hybrid AI-human security is no less important, as it provides Human-in-the-Loop Security, combining human expertise with AI analysis for threat detection and overall Human Oversight, which helps ensure AI decisions are subject to human review.
What Measures Can Be Taken?
Using AI security to prevent IoT and IIoT attacks demands a multifaceted approach. It's crucial to handle data with specific care, making sure it is used responsibly in AI models. Moreover, it is important to protect personal data by preventing unnecessary uploads from the user end.
The examples of Smart gadgets’ susceptibility teach us that consistently updating and patching vulnerabilities on user endpoints such as mobile devices, laptops, and IoT devices is essential.
Furthermore, corporate responsibility comes to the fore. AI companies must understand and incorporate a deep sense of global responsibility. While instilling this sense through moral imperatives might be challenging, immediate legislative and regulatory measures can bridge the gap. Extrapolating it to a broader level, legislative revision is also paramount.
Other than that, unnecessary AI access to the IoT sphere should be restricted, ensuring only necessary and secure interactions.
Finally, I shall insist on the triple emphasis on Security. Security, Security, and once again, Security reiterates the supreme importance of safeguarding systems. Just as IT security, InfoSec, and Cybersecurity have their critical roles, AI Security is now joining the ranks. AI Security types must be paired with the above solutions, ensuring comprehensive protection across all fronts.
Opinions expressed by DZone contributors are their own.

Comments