DevSecOps takes a very agile approach to security, breaking down massive security tasks into incremental improvements that are performed as everyday development tasks. These small batches of work include continuous verification so that security builds over time instead of repeatedly starting from scratch.
DevSecOps brings a culture of “security for everyone” to teams. Everyone has a significant role to play in security at their organization. Security specialists are critical in this by mentoring, advising, and leading teams to ensure quality and security.
Once we’ve identified the next security challenge, our normal engineering process can execute on the improvement. In this section, we explore four core practices to any DevSecOps initiative. Of course, your DevSecOps process might be considerably more complex. See the next section for more ideas, or add your own practices to this basic cycle.
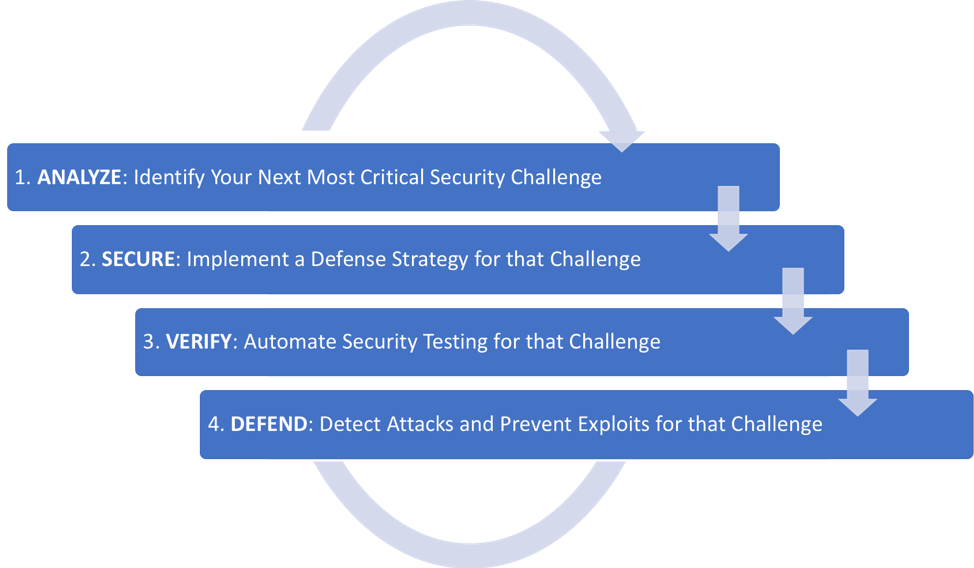
Fundamentally, it is the constant tension between creating defenses and attempting to break them that actually makes organizations more secure. The faster you can repeat this DevSecOps cycle, the faster you can improve security. Over time, you’ll build a complete security story that will provide assurance both internally and externally.
1. ANALYZE: Identify Your Next Most Critical Security Challenge
Why should one always focus on the most critical security challenge? Generally, working on anything else won’t change your security posture very much. It doesn’t help to close the attic window when the garage and front door are wide open. In DevSecOps, we get the work flowing by creating small batch sizes. So, in most cases, we want to work on our enterprise's most critical security challenge first. Still, don’t be afraid to choose a partial measure or a tiny improvement to your most critical challenge. Working in small increments makes sure we stay on track.
When deciding what to work on next, the team looks at all the potential security “work” available and makes it visible. The team might add new features, pay down some technical debt, make an architectural improvement, fix defects/vulnerabilities, or do something to improve the team’s tools or practices to improve quality, security, or productivity.
It’s important that the team use its threat model and security architecture to make an informed decision about the next most critical security challenge. What is the cost to the company of certain kinds of attacks? What is the cost of implementing preventive measures for those attacks? Try to use both internal and external data sources to figure out the next thing to do that will most effectively reduce risk.
You may find yourself without a threat model or security architecture. Fortunately, in DevSecOps, these artifacts are created one step at a time. When you’re starting out, it’s easy to identify your top challenges: the problems that are the most likely to be found, exploited, and cause serious damage like injection, authorization problems, known vulnerabilities, etc.
Consider all the different layers of your application stack:
Security Considerations for Layers of the Application Stack |
Layer |
Consideration(s) |
Applications
and APIs |
Do you have proactive controls in place? Are you susceptible to common vulnerabilities? |
Libraries and frameworks |
Are your libraries and frameworks up-to-date and properly configured? Do you have a complete, up-to-date inventory (with exact version numbers) of all the software you are running across all your servers? |
Containers |
Have you hardened your platform configuration and kept it up to date? Are your cloud environments configured correctly? Did you consider scanning container images against vulnerabilities? Did you add security scans to your pipeline? |
Cloud resources |
Are applications and customer data secure? Do we have an authorization matrix in place to make sure the right people have the right access? Are networking configurations configured properly for each resource? Do we have the penetration test results on public-facing resources? |
Network |
Do you have strong network security defenses in place and monitored for attacks? |
Use a risk-based approach to decide what to work on next. Be sure to consider whether there’s a viable connection between a threat agent, attack vector, weakness, technical impact, and business impact in your enterprise. OWASP depicts this connection as follows:
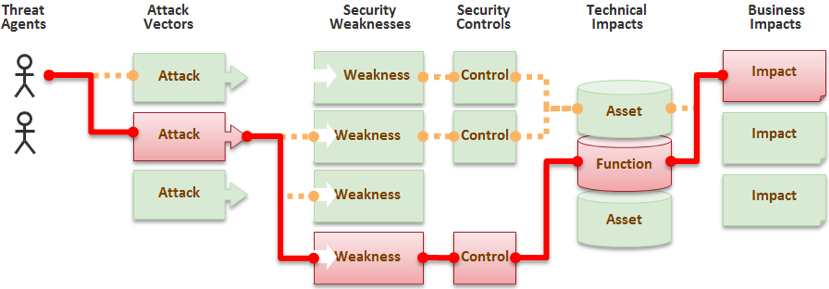
Going forward, you should practice a combination of threat intelligence and security research to continuously zero in on your next most critical security challenge. Note that this process is significantly different from assessing all your threats. Many organizations get overwhelmed trying to protect against everything at once.
DevSecOps Threat Intelligence, Security Research, and Security Architecture |
Threat intelligence |
External sources: ISACs (STIX/TAXII), OWASP, SANS, BlackHat, DefCon, LASCON, DevSecCon, CISO events, friendly peer companies, etc. Internal sources: Monitor your systems for attacks and learn from the data. Understanding actual attacks is a major factor in prioritizing. |
Security research |
Security research should focus on challenging security architectures and identifying new strategic ways to improve security. Where possible, work with development to enhance the DevSecOps pipeline with new testing methods. |
Security architecture |
There is a shortage of great threat modeling and security architecture tools. But some interesting projects include OWASP Threat Dragon, IriusRisk, and Chaos Engineering (Chaos Monkey, ChaoSlingr). |
You’ll have to work out your own cadence for re-examining your threat model. So, increasing your cycle speed will directly affect the level of security you are able to achieve. And because DevSecOps adds to your security incrementally with continuous security verification (discussed below), you have protection against backsliding.
2. SECURE: Implement a Defense Strategy
Once you’ve decided on a security challenge to tackle, you’ll need to choose a defense strategy. A defense strategy isn’t a single security mechanism or product. A defense strategy can combine technical security mechanisms, secure coding practices, procedural controls, supporting processes, training, background checks, and more. We are using the term “defense strategy” broadly to include anything that you rely on to prevent a breach. Your defense strategy for a particular challenge can (and probably should) comprise one or more primary defenses and a set of supporting defenses as well.
In an agile way, you have defined stories and tasks for each sprint. The product owner is the person who defines new feature requests and also the priority level. This usually applies to application features and not security. In a DevSecOps approach, security is also considered a high-priority feature added to the backlog. Security specialists give consults on what needs to be done, and all team members can participate in the implementation, test, and delivery. This approach prevents teams from having security silos, and security expertise is shared between all team members from developers to testers and DevOps engineers.
You can capture each security strategy for implementation in a JIRA ticket that covers each security enhancement that you want to make, including:
DevSecOps Defense Strategies |
Strategy |
Description |
Challenge description |
The goal is to justify why this is an important security challenge concisely. This might take the form of a security story or misuse case. The description should cover the elements shown in the OWASP diagram above. |
Defense story |
This story should detail exactly how the defense should work. For technical defense mechanisms, the story should clearly detail how the threat is countered and why this defense is effective. For other defenses, how they work to provide protection should be argued. |
Documentation |
As part of the defense strategy, you should also consider how to configure, operate, and use these defenses. This guidance should be written as a tutorial to apply to end-users and operations staff, and even indicate how developers should use the defense effectively. It is vital to document all operations and implementations to prevent any rework in the future. |
Security testing approach |
It is important to define automated tests, which verify the correctness and effectiveness of the defense strategy. |
Fail and test your system |
Do not wait for disaster to strike in order to verify security effectiveness. Instead, try to fail the system and challenge implementations yourself. This can be done on environments other than production, where you may have a clone production environment like an acceptance environment. Simulate security issues to see if the defense strategy works as expected. |
Security monitoring |
The final part of the defense strategy is to detail how to will continuously monitor security and avoid possible attacks. |
Your strategy is right when you can easily answer with confidence when anyone asks: “How do you protect against X?” Having a clear, concise, defensible answer to this kind of question can not only provide an easy path to compliance but can also provide business advantages over competitors.
Your defense strategy doesn’t have to be perfect from the very start. It’s far better to start with a basic defense and evolve it over time. After you implement a basic defense, you may choose to work on another, more pressing, threat. The key to DevSecOps is to continuously reprioritize based on the threat and existing defenses. The ability to respond quickly is critical for a world of continuously changing threats.
The work of implementing the security defense shouldn’t be any different than any other feature. It should — to the maximum extent possible — be delivered as code or configuration with everything in source control. Managing security in this way makes it possible to test and redeploy at any time, ensuring that defenses are in place, working correctly, and properly configured.
3. VERIFY: Automate Security Testing
A key part of DevSecOps is ensuring that the defense strategies have been properly implemented, configured, and operated. Security testing is how to verify that your actual security controls match your intended defenses. In DevSecOps, we focus on automating those tests by “turning security into code” so that we can run them frequently without requiring humans, particularly security experts, in the critical path.
There are many ways to verify the security of a system automatically. There is no possible way to list them all, but we provide a few examples of popular tools that have proven to be DevSecOps compatible.
Popular DevSecOps Automation Techniques |
Technique |
Description |
Automate everything |
It's not automated if you need humans in the loop. Don't fall into the trap of thinking that you've automated security when all you really did was automate the "scan" button. Think about the entire process. Does the tool require human expertise to configure or run? Does it require an expert to interpret and triage the results? We are looking to eliminate the involvement of humans in the critical path so that we can push code to production with both speed and assurance. |
Avoid “tool soup” |
Every tool that you adopt means additional process steps, a full set of integrations, and a team of people to configure, run, and interpret. Choose powerful platforms that will allow you to address many different types of security challenges using an integrated framework. Therefore, you avoid having overhead when maintaining multiple tools. |
Test your testing tools |
Security testing tools vary significantly in their ability to test real applications for a broad range of issues. The only way to know how well a particular tool will work on your applications and APIs is to try it. Consider temporarily adding “tool canaries” in your applications to verify that real vulnerabilities are being discovered and false alarms are not being flagged. See the OWASP Benchmark project for details. |
Below is a DevSecOps security testing funnel to help you choose a security verification technique for a particular security challenge. This may seem obvious, but don’t blindly rely on the wrong tool. Take a minute to select the simplest, fastest, most accurate way to check that your defense implementation is correct, complete, and configured.
For example, testing for proper clickjacking protection is easy if you simply examine HTTP responses for the proper security headers. But it would be very difficult to verify this by looking at the source code, as there are so many ways to accomplish this.
DevSecOps Security Testing Funnel |
What are we trying to test? |
Think carefully about exactly what you want to test and the results you want. Direct, complete verification of application behavior is always best, but you can use sampling, fuzzing, design analysis, and other techniques. |
Do we need to test it? |
Probably, yes. But you should clearly prioritize things that are the most critical to security and the most likely to be discovered and exploited by an attacker. |
Positive or negative testing? |
Are we able to verify that the application always follows a known good pattern of execution (positive security), or will we have to resort to trying to verify that the application never follows any of the known bad patterns of execution (negative security)? |
Do we already test for it? |
You may be using a security testing tool that covers this risk. It's critical to confirm that your tool does a good job of accurately and efficiently verifying your security defense. |
Do we already have a platform that will allow us to test this easily? |
Perhaps you just need to enable a rule in a tool you're already using. Or maybe you can use an existing tool as a platform for creating a custom rule. |
Can we test it by writing custom tests? |
If we can't use a security testing platform, can we create a custom test case? |
Is there another tool on the market that can help test this? |
- Network: nmap, sslyze, ssh_scan, Tenable, Qualys.
- Cloud/container: Aqua, Twistlock, Redlock, ThreatStack.
- Libraries/frameworks: OWASP Dependency Check, retire.js, Contrast Assess, Snyk, Sonatype, BlackDuck.
Application: OWASP ZAP, Arachni, sqlmap, Burp, Contrast Assess, Micro Focus, CA Veracode, Synopsys, Checkmarx. |
Do we need human experts to test it? |
While the goal of DevSecOps is to minimize the number of things that you need human experts to test, bug bounties, red team exercises, and manual penetration testing can provide useful insight into defenses that are difficult to test automatically. Ensure that these efforts deliver rules, test cases, and other automation, not PDF reports. Examples: BugCrowd, HackerOne |
Are we also testing for what we didn’t think of? |
It’s impossible to know everything, so certain kinds of testing rely on volume and randomness to try to force applications to misbehave. Fuzz testing and chaos engineering tools can help here. |
Any security issues discovered during testing should feed into the DevSecOps management infrastructure described above to notify all the people that need to know through the tools they are already using.
4. DEFEND: Detect Attacks and Prevent Exploits
DevSecOps organizations recognize that you can never test yourself securely, so they adopt a balanced approach that focuses on minimizing vulnerabilities during development and identifying and preventing vulnerabilities from being exploited in production. While these two activities have traditionally been separated, DevOps has brought them together by supporting the full software lifecycle.
DevSecOps Attack Detection and Prevention Tools |
Tool |
Description |
Runtime Application Self Protection (RASP) |
RASP uses application instrumentation to add attack detection and prevention directly to applications regardless of where or how they are deployed. DevSecOps projects can use RASP to achieve accurate attack-blocking and the flexibility to deploy in cloud/container environments easily. Examples: Contrast Protect, Prevoty, Immunio. |
Web Application Firewall (WAF) |
WAFs have been on the market since the early 2000s and have a history of complex configuration and spotty protection. Nevertheless, a DevSecOps project might be able to use a WAF for basic protection or as a platform for virtual patches. Examples: ModSecurity, Imperva, F5, Signal Sciences. |
Network Intrusion Detection and Prevention (IDS/IPS) |
There is a variety of network-, container-, and host-level protections against attacks. Seek out products that can be deployed and managed as part of your standard technology stack. Examples: Snort, Suricata, Bro, Kismet. |
Security Information and Event Management (SIEM) |
SIEM tools provide real-time analysis of security alerts generated by applications and network hardware and are important to handling attacks in DevSecOps. Examples: Splunk, ELK, SumoLogic, LogRhythm, ArcSight. |
The threat and attack data gathered should feed directly into the next DevSecOps cycle to use security research to help choose the next most critical security challenge.



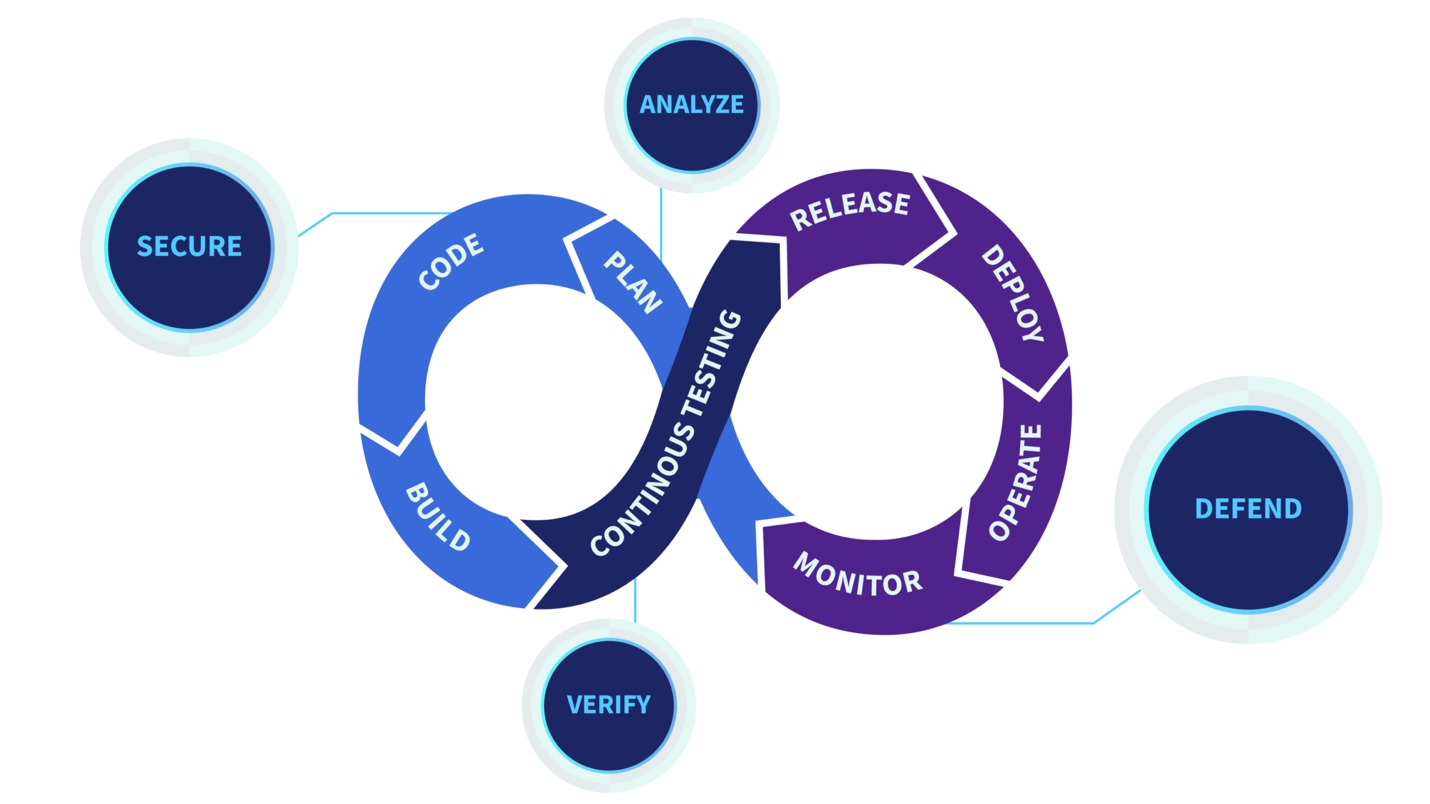
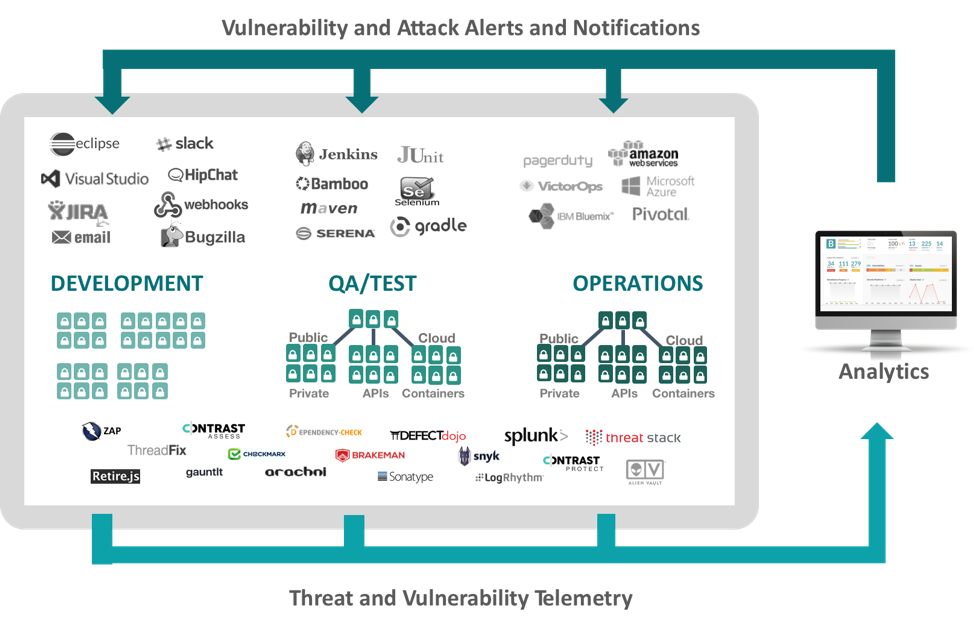


{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}
{{ parent.urlSource.name }}