Securing Your CI/CD Pipeline
In this article, learn about common CI/CD security challenges and advanced strategies to mitigate threats.
Join the DZone community and get the full member experience.
Join For FreeThis is an article from DZone's 2022 DevOps Trend Report.
For more:
Read the Report
Software firms have long relied on a DevOps approach to enhance agility and collaboration in software delivery. CI/CD pipelines automate processes in the software development lifecycle (SDLC) to enable seamless integration and delivery of new features. While CI/CD pipelines enhance software development through automation and agility, they involve integrating numerous tools and services, which can introduce security gaps. Identifying and remediating these security gaps is key to ensuring secure CI/CD practices. This article presents a general overview of what you need to know as you secure your CI/CD pipeline.
Introduction to CI/CD Security
While CI/CD pipelines enhance the efficiency of software development and delivery through automation, the core stages of the pipeline don't include security by default. CI/CD security is the set of practices aimed at identifying and fixing vulnerabilities without significantly slowing down processes in the pipeline. CI/CD security practices mainly involve injecting penetration tests and active security audits to help reduce bottlenecks caused by late handoffs to security and QA teams. Secure CI/CD pipelines enable software teams to automate security for multiple deployment environments and layers of the SDLC, enforcing agility.
Common Security Threats for a CI/CD Pipeline
Each organization's CI/CD pipeline has unique characteristics based on the business case, workload, and tech stack used. As a result, the implementation of CI/CD security differs based on use case. There are, however, security risks that are common to almost all pipelines, which warrant similar identification and remediation approaches. These risks include:
Unauthorized Access to Code Registries
CI/CD operations rely on shared repositories to enable collaboration, configuration management, updates, and version control. All source code and configuration files reside on the Git repository as a single source of truth. Public repositories are popular in modern CI/CD pipelines since they reduce development costs and time. These repositories pose a security threat, however, as developers publish source code from their private machines into public, shared folders. Attackers can search through open-source registries as a reconnaissance technique and leverage the data gained for targeted phishing, reverse engineering, and remote code execution attacks.
Insecure Code
The requirements of rapid development and delivery in CI/CD pipelines have led to the increasing use of open-source, third-party integrations. Some teams may import third-party integrations into the deployment environment without properly scanning the source code for security gaps. These integrations can introduce vulnerabilities into the CI/CD pipeline. Developers may also fail to follow best practices for code security, which increases the attack surface. Common code vulnerabilities include format string vulnerabilities, buffer overflows, improper error handling, and canonicalization issues, among others.
Improper Secrets Management
Secrets aid in managing access to data and resources within the CI/CD pipeline. These include passwords, tokens, API keys, and other authentication credentials used to validate users accessing sensitive systems in the pipeline. Exposed secrets can, therefore, grant an attacker control over part or all of the CI/CD processes. Secret management misconfigurations include hard-coded secrets, storing secrets in public cloud environments, and manual secrets management, among others.
Shifting Security Left
In older pipelines, security was often a final step, contributing to deployment bottlenecks. Today, best practices require integrating security controls earlier in the SDLC, otherwise known as "shift security." Shifting left involves implementing security checks in every layer of the CI/CD pipeline, enabling more accurate threat detection in every step. The goal is to remove friction between DevOps and security teams, enhancing efficiency in software development and ensuring robust security practices.
Key Considerations for Adopting a CI/CD Security Tool
Some factors to consider when selecting a tool to secure the CI/CD pipeline include:
- Scanning coverage
- Ownership costs and licensing terms
- Maintenance and configuration effort required
- Scalability
- Integration with existing development and security stack
Administering Security on a CI/CD Pipeline
With the changing threat landscape, administering security is one of the most crucial aspects of a CI/CD pipeline. The first step in securing DevOps workflows starts with assessing how you can apply the principles of DevSecOps to your CI/CD pipelines. One of the goals of a diligent assessment is to identify tools and strategies to administer robust security.
Best Practices To Secure a CI/CD Pipeline
To fully realize the benefits of integrating security directly into the software lifecycle, teams should:
Avoid Hardcoding Secrets in Config Files and CI/CD Build Tools
Secrets are often required at various stages of the SDLC. An easy way to provide these secrets is to reference them as environment variables in configuration files and manifests. Anyone who can access these templates and files can extract credential information from these files, potentially leading to a data breach. Software teams should use tools that encrypt, store, and enable the central management of secrets to keep credential data away from malicious users. To securely manage and distribute secrets, administrators should perform encryption at rest before storing them in the ETCD server.
First, encode the secrets in Base64 format as shown below:
$ username=$(echo -n "admin" | base64)
$ password=$(echo -n "a62fjbd37942dcs" | base64)Define the secrets in a YAML file:
echo "apiVersion: v1
> kind: Secret
> metadata:
> name: test-secret
> type: Opaque
> data:
> username: $username
> password: $password" >> secret.yamlNext, once secrets are created, you can use those to be applied into a Kubernetes pod. This can be done by creating a .yaml file, secret-env.yaml, whose environment variables are populated with data from the secret. The file's specs would be similar to the following:
apiVersion: v1
kind: Pod
metadata:
name: secret-env-pod
spec:
containers:
- name: mycontainer
image: alpine:latest
command: ["sleep", "9999"]
env:
- name: SECRET_USERNAME
valueFrom:
secretKeyRef:
name: test-secret
key: username
- name: SECRET_PASSWORD
valueFrom:
secretKeyRef:
name: test-secret
key: password
restartPolicy: NeverWhen populating environment variables, Kubernetes decodes Base64 values. These environment variables can be used in all Kubernetes API objects, eliminating the need to hardcode secret data.
Enforce Access Controls for CI/CD Build Tools
DevOps teams should implement authentication and authorization mechanisms to control the entities that can access specific processes and tools within the CI/CD pipeline. The teams should enforce the principle of least privileges to ensure resource access is only granted to those who absolutely need it. Data within the CI/CD pipeline should also be secured using tokens, access keys, and passwords to prevent the addition of malicious payloads into the pipeline.
Establish Authentication Mechanisms for Source Control
Version control repositories (most often in Git) are a must-have for CI/CD pipelines. They foster collaboration and enable continuous deployment of features. Since the Git repository contains the application's source code, Infrastructure-as-Code manifests, and intellectual property, a vulnerability in source control grants attackers access into the application's design and implementation logic. Access to Git repositories should be secured using multi-factor authentication since they are a high-value target for hackers. Teams can also prevent accidental branches and commits using the .gitignore file, and educate developers on Git best practices.
Ensure Configuration Parity Across All Environments in the Pipeline
DevOps teams should ensure that all environments (development, testing, production, and so on) are configured similarly. With configuration parity, QA teams can accurately detect security issues during testing as these issues exist on all environment configurations. This parity can be achieved using virtualization and abstraction technologies like containers and Infrastructure-as-Code declarations.
Configure Rollback Capabilities
It is common for security and QA teams to uncover security issues after application updates or deployments. This requires the administrators to roll back (revert) the deployment to an earlier version. The deployment should be configured to achieve a graceful rollback that eliminates the security issue until the development team has worked on it. Rollbacks are best achieved by retaining artifacts of an older version until the new deployment is approved for production.
Implement Continuous Vulnerability Scanning and Monitoring
It is important to monitor and test every resource in the CI/CD pipeline. Use a vulnerability scanning solution to test application code, environment configurations, and deployment scripts against a database of known vulnerabilities to eliminate potential attack vectors. These scanning and monitoring tools should be deployed across the entire SDLC to uncover vulnerabilities as soon as they occur to prevent exploits.
Clean Up Redundant Resources and Utilities Frequently
CI/CD pipelines are typically built with immutable infrastructure, which run specific processes and then terminate. DevOps teams should ensure all temporary resources such as containers, services, and virtual machines are cleaned up after termination. Attackers could use their open ports to gain initial entry into the deployment environment, so it's important to properly manage these resources to reduce the security gap.
Layers of CI/CD Security
Administering CI/CD security requires a comprehensive, multi-layered approach to strengthen the defense across every point on the pipeline. These layers of security include:
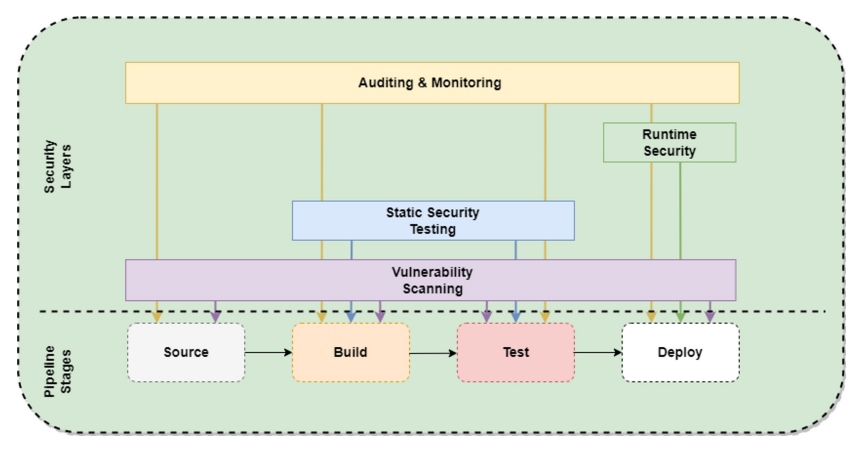
Security layers in a secure CI/CD pipeline
Vulnerability Scanning
Vulnerability scanning involves using databases of known threats to identify and remediate security gaps in the entire CI/ CD pipeline. Automated tests scan the application and deployment environment to identify and classify weaknesses in code, infrastructure, and third-party services.
Static Security Testing
These are software composition analysis techniques aimed at identifying potential vulnerabilities in code written by internal development teams. Security teams often use these tools to develop test cases to pinpoint insecure code vulnerabilities before deploying new application builds.
Runtime Security
This layer relies on runtime application self-protection (RASP) tools to detect security threats for applications in live production environments. These tools scan configuration templates and continuously test the state of the deployment environment, then use a comparison to identify and respond to any runtime threats.
Auditing and Monitoring
Application and infrastructure logs continuously track and store application and deployment data. Auditing involves analyzing these logs to infer patterns that can be used to improve the application's security posture. Monitoring is the deployment of diagnostic tools that analyze metrics to gain an understanding of most system-related issues.
Constant auditing and monitoring help teams build context and predict baseline user behavior. Security teams can identify security threats by analyzing user actions that deviate from the established baseline.
Conclusion
As code that runs in a CI/CD pipeline can be executed by anyone with access to the pipeline's source code repository or container registry, DevOps workflows are known to introduce inherent security challenges. A recent survey projected that roughly 55 percent of organizations delay application rollouts due to security concerns. While a DevOps framework enables enhanced collaboration and automation, organizations must adopt a continuous security model that considers advanced strategies and tools to ensure comprehensive security across all layers of a CI/CD pipeline.
This is an article from DZone's 2022 DevOps Trend Report.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments