Teams can mitigate or completely remove threats and security vulnerabilities with the following core concepts.
Docker Networking
Docker’s networking is a complex part of the Docker infrastructure, and it is essential to understand how it works. It’s important to know what Docker Network Drivers are, for example:
By default, one container network stack does not have access to another container. However, if you configure a bridge or host to accept traffic from any other containers or external networks, you can create a potential security backdoor for an attack. You can also disable inter-container communication using a set flag — icc=false within Docker daemon.
Set Up Resource Limits
It’s important to set up memory and CPU limits for your Docker container because Docker has a container that does not provide this option by default. This principle is an effective way to prevent DoS attacks. For example, you can set up a memory limit to prevent your container from consuming all memory. The same applies to CPU limits. Additionally, there is an option to set up resource limits on a Kubernetes level — this will be covered in greater detail in the Kubernetes Hardening Guidelines section below.
Avoid Sensitive Data in Container Images
This principle is quite important to move all sensitive data out of the container. You can use different options to manage your secrets and other sensitive data:
- Docker secrets allows you to store your secrets outside of the image.
- If you run Docker containers in Kubernetes, use Secrets to store your passwords, certificates, or any other sensitive data.
- Use cloud-specific storage for sensitive data — for example, Azure Key Vault or AWS Secrets Manager.
Vulnerability and Threat Detection Tools
Vulnerability scanning tools are an essential part of detecting images that may contain security pitfalls. Moreover, you can also integrate properly selected tools into the CI/CD process. Third-party vendors and some common open-source tools offer this sort of functionality. Some examples of these open-source tools can be found in the About Container Security and Threat Detection section.
Container Registries
To protect your images, create an additional security layer and use images from protected registries. Here are a few examples of open-source registry platforms:
- Harbor – An open-source registry with integrated vulnerability scanning. It is based on security policies that apply to Docker artifacts.
- Quay – An open-source image registry that scans images for vulnerabilities. Powered by RedHat, Quay also offers a standalone image repository that allows you to install and use it internally in your organization. Below, we will dive into how it scans for vulnerabilities within containers.
Principle of Least Privilege
This principle means that you should not execute containers using admin users. Instead, you should create users that have admin access and can only operate with this particular container. Groups can also add users there. Read more about it in the Docker Engine Security documentation. Below is an example of how to create the user and group:
RUN groupadd -r postgres && useradd --no-log-init -r -g postgres postgres
USER postgres
Also, alongside creating users and groups, please be sure to use the official verified and signed images. To find and check images, use docker trust inspect. Find more options and tools in the section below: Threat Detection Tool Selection Criteria for Containers.
Linux Security Module
To enforce security, implement the default Linux security profile and do not disable the default one. For Docker, you can use AppArmor or Seccomp. Security context rules in Kubernetes can also be set up with allowPrivilegeEscalation. This option controls the privileges that the container possesses. Also, the readOnlyRootFilesystem flag sets the container root filesystem to read-only mode.
Static Image Vulnerability Scanning
Now that we know how threat detection tools can work together and the strategies that we can use, let’s define what it means to adopt static image vulnerability scanning, secret scanning, and configuration validation. Static security vulnerability scanning is based on the Open Container Initiative (OCI) format. It validates and indexes the images against well-known threats and vulnerability information sources, like CVE Tracker, Red Hat security data, and Debian Security Bug Tracker.
Static security vulnerability scanning mechanisms can be used for scanning several sources, like:
- Container image
- Filesystem and storage
- Kubernetes cluster
Static image vulnerability scanning can also scan misconfigurations, secrets, software dependencies, and generate the Software Bill of Materials (SBOM). An SBOM is a combination of open-source, third-party tools and components within your application that contains license information of all components. This information is important for quick identification of security risks.
Below, we’ve included a list of open-source tools that cover the logic explained above. This is a representation of only a few of the many tools that can be used:
- Clair – A security vulnerability scanning tool with an API for development integration purposes. It also creates your own divers to extend and customize Clair functionality. Clair has several Indexer, matcher, notifier, or combo models.
- Trivy – A security container scanner based on the CVE threat database. Trivy can be installed on your PC or in the Kubernetes nodes, using
npm, apt-get, brew, and other package managers, like:
apt-get install trivy yum install trivybrew install aquasecurity/trivy/trivy
To execute image scanning, run the following command:
$ trivy image app-backend:1.9-test
Another key to static image vulnerability scanning is the Security Content Automation Protocol (SCAP). SCAP defines security compliance checks for your infrastructure based on Linux. OpenSCAP is a tool that includes complex security auditing options. It allows you to scan, edit, and export SCAP documents, consisting of the following components and tools:
- OpenSCAP Base – For vulnerability and configuration scans
oscap-docker – For compliance scans- SCAP Workbench – A graphical utility to facilitate the execution of typical OpenSCAP tasks
Below, you can see an example on how to run the validation process of the SCAP content:
oscap ds sds-validate scap-ds.xml
Configuration Validation
Static image validation is an important part of the threat detection process. However, static image scanning cannot detect the misconfiguration in the YAML and JSON configuration, and it may cause outages in complex YAML configs. Therefore, having an easy and automated method involves configuration validation and scanning tools like Kubeval. We can introduce configuration validation that can solve issues with static configuration and simplify the automation process.
As an example, we will incorporate Kubeval, an open-source tool used to validate one or more Kubernetes configuration files, often used locally as part of a development workflow and/or within CI/CD pipelines.
To run the validation, use the following example:
$ kubeval my-invalid-rc.yaml
WARN - fixtures/my-invalid-rc.yaml contains an invalid ReplicationController - spec.replicas: Invalid type. Expected: [integer,null], given: string
$ echo $?
1
Secrets Scanning
The main goal of secrets scanning is looking into the container images, infrastructure-as-code files, JSON log files, etc. for hardcoded and default secrets, passwords, AWS access IDs, AWS secret access keys, Google OAuth Key, SSH keys, tokens, and more.
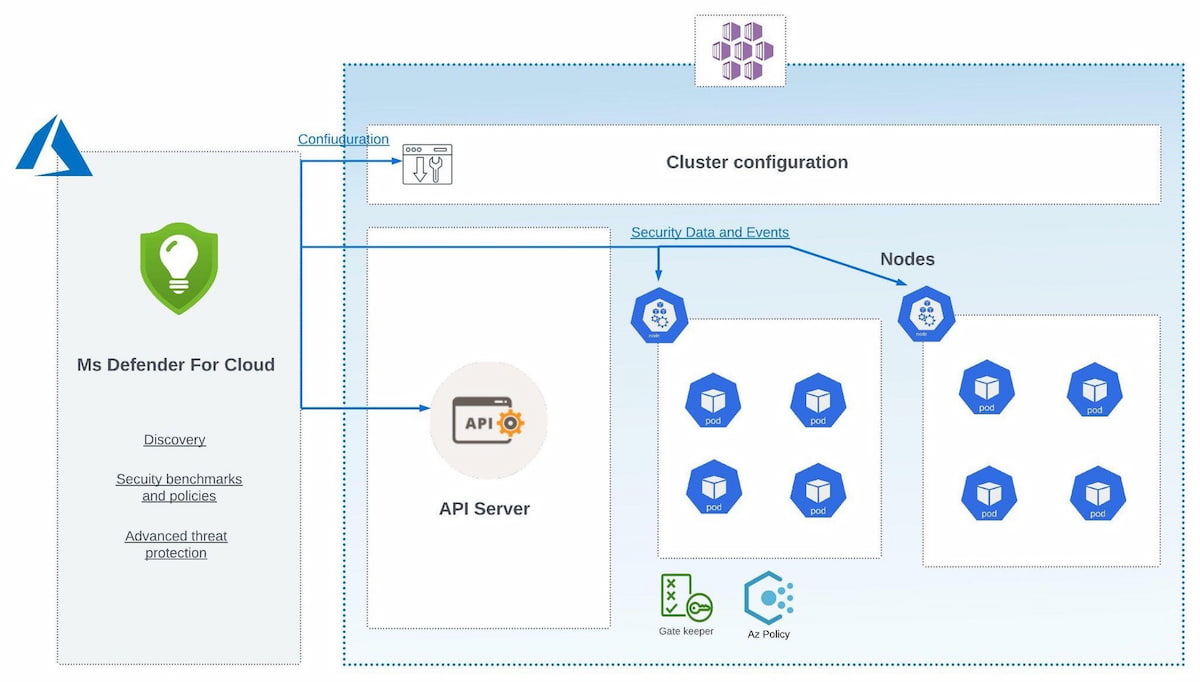
Management Console and Sensor Agents
A management console is a UI tool that builds a security infrastructure overview and provides vulnerability and threats reports. On the other hand, sensor agents are a tool that scans cluster nodes and gathers security telemetry. Thus, sensor agents report telemetry to the management console.
For example, to install sensor agents within the AKS cluster, adhere to the following:
helm repo add deepfence https://deepfence-helm-charts.s3.amazonaws.com/threatmapper
helm show readme deepfence/deepfence-agent
helm show values deepfence/deepfence-agent
# helm v2
helm install deepfence/deepfence-agent \
--name=deepfence-agent \
--set managementConsoleUrl=x.x.x.x \
--set deepfenceKey=C8TtyEtNB0gBo1wGhpeAZICNSAaGWw71BSdS2kLELY0
To install the management console within your AKS cluster, use the following command:
helm repo add deepfence https://deepfence-helm-charts.s3.amazonaws.com/threatmapper
helm install deepfence-console deepfence/deepfence-console
The installation completes two operations:
Both commands are quite simple and can be easily integrated into an IaC process.


{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}
{{ parent.urlSource.name }}